A 51% attack in crypto is one of the most feared security threats the world has seen.
It occurs when a single entity gains control of more than 50% of a blockchain’s mining power, allowing it to manipulate transactions, double-spend coins, and undermine the integrity of the network.
Although rare, 51% attacks have happened before—impacting several blockchains, especially smaller ones with lower hash rates.
In this article, we’ll break down:
- What a 51% attack is
- How it works
- Real-world cases of 51% attacks
- The risks and consequences
- How crypto networks can prevent these attacks
Let’s dive in.
What is a 51% Attack in Crypto?
🔹 A 51% attack can cripple a blockchain by allowing attackers to double-spend and manipulate transactions. Learn how these attacks work, real-world cases like Bitcoin Gold & Ethereum Classic, and how to prevent them.
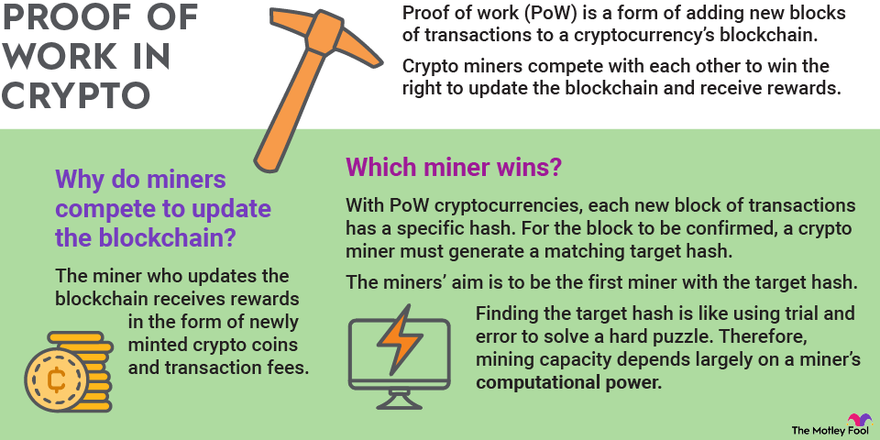
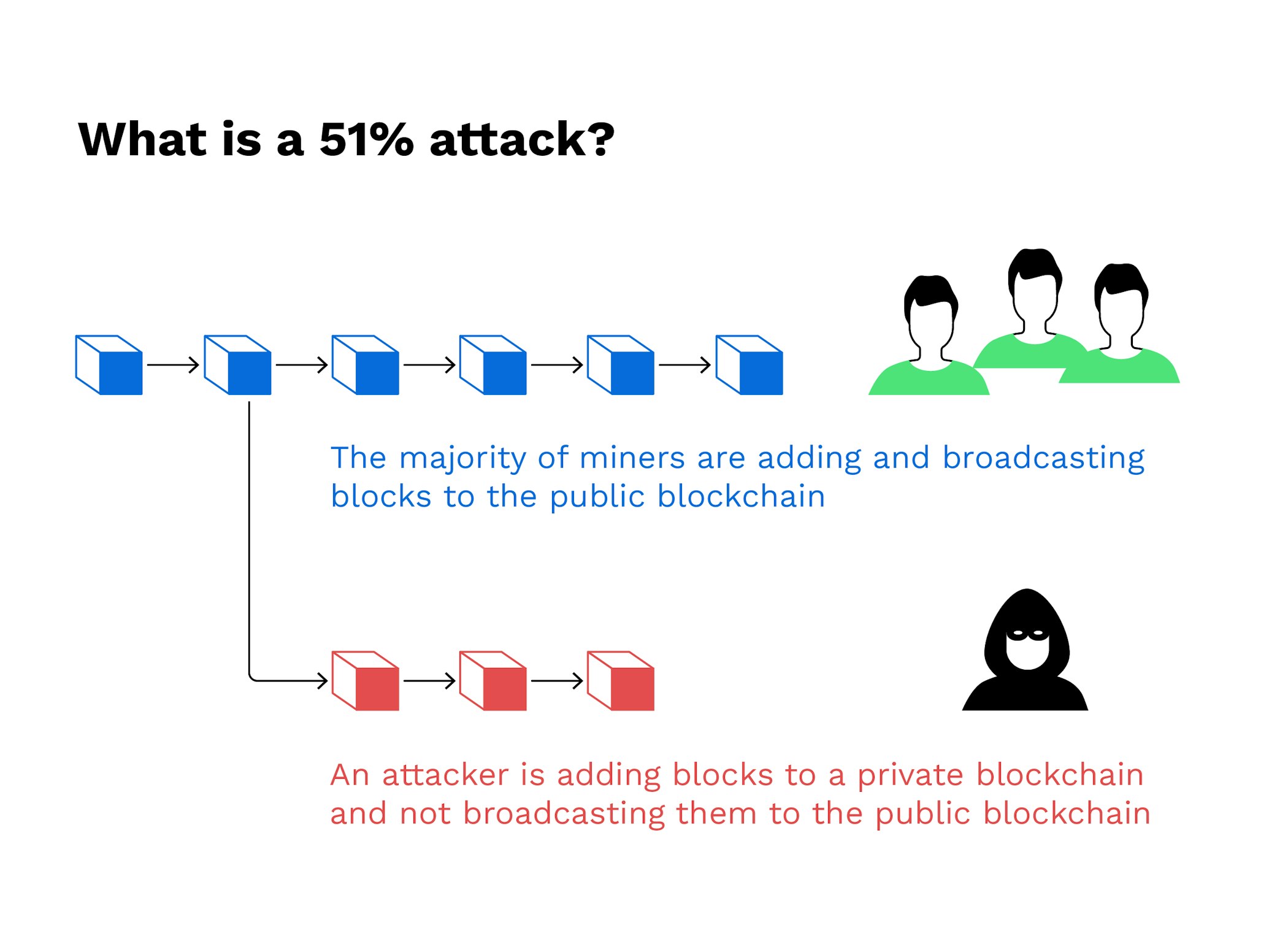
A 51% attack occurs when a single miner or a group of miners gain more than 50% of the computational power in a Proof-of-Work (PoW) blockchain.
This dominance allows the attacker to manipulate the ledger by:
✅ Double-spending – Reusing the same cryptocurrency for multiple transactions.
✅ Reorganizing transactions – Changing or reversing transactions in past blocks.
✅ Blocking new transactions – Preventing new transactions from being confirmed, effectively stopping payments.
However, a 51% attack cannot:
❌ Print new coins out of thin air.
❌ Steal funds from other wallets.
❌ Alter past transactions before their takeover.
This attack is primarily a risk for PoW blockchains like Bitcoin, Ethereum (before switching to PoS), and others.
How Does a 51% Attack Work?
To understand how a 51% attack happens, we need to explore blockchain mining and consensus mechanisms.
1. The Role of Mining in PoW
In a PoW system, miners compete to solve complex mathematical problems.
The first one to solve it gets to add a new block to the blockchain and earns rewards.
The more mining power (hash rate) a miner has, the more chances they have to win.
2. The Importance of Longest chain Rule
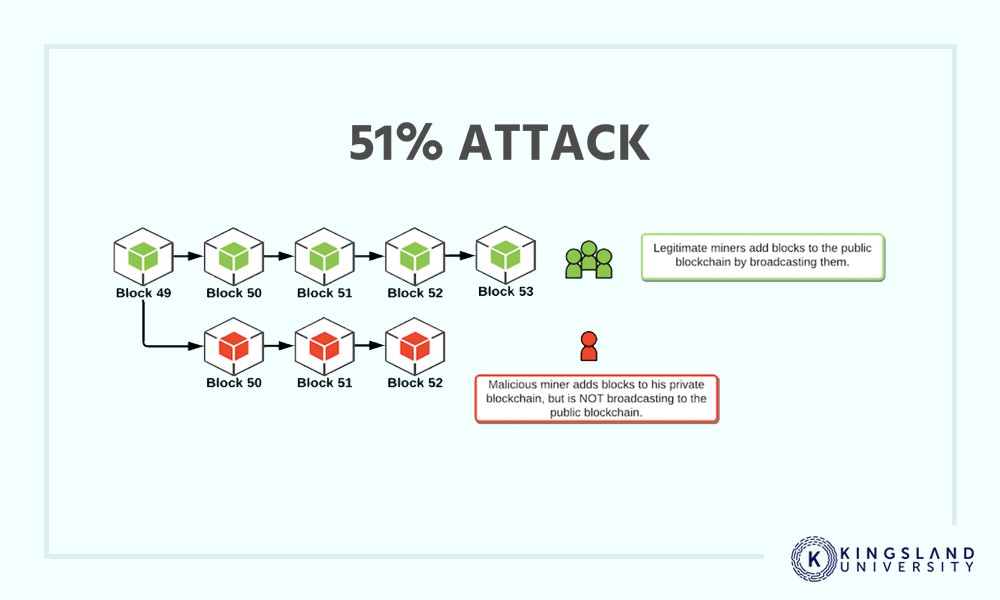
Blockchains follow the longest chain rule—the longest valid chain is always considered the true version of the ledger.
If an attacker controls 51% of the hash power, they can mine faster than the rest of the network combined.
3. Executing the Attack
A 51% attack works in the following way:
- The attacker secretly mines a private chain – They start mining blocks in private while the public network keeps running as usual.
- They double-spend coins – They send some of their coins to an exchange and trade them for another asset.
- They release their private chain – Since they control more than 50% of the mining power, their chain is longer than the public blockchain.
- The network accepts their version of events – The shorter chain is discarded, meaning their original transactions are erased, and they keep both the spent coins and the new assets from the exchange.
This damages trust in the network and can lead to financial losses for users.
Real-World 51% Attacks
While 51% attacks are rare in large and well-established networks like Bitcoin, they have occurred multiple times in smaller blockchains, especially those with lower hash rates.
These attacks have led to millions in losses, shaken investor confidence, and, in some cases, caused severe damage to the reputation and adoption of affected cryptocurrencies.
1. Bitcoin Gold (BTG) – 2018 & 2020 Attacks
The 2018 Attack
Bitcoin Gold (BTG) is a fork of Bitcoin designed to make mining more accessible by using a different algorithm called Equihash, which is optimized for GPU mining rather than ASICs.
However, this approach made it vulnerable to attacks, as Equihash-compatible mining rigs could be rented from cloud mining services.
In May 2018, Bitcoin Gold suffered one of the most devastating 51% attacks in history. The attackers controlled a majority of the network’s hash rate and executed a double-spending attack that targeted cryptocurrency exchanges.
The attackers first deposited large amounts of BTG into various exchanges. Once their deposits were confirmed, they traded their BTG for Bitcoin or other cryptocurrencies and withdrew their funds.
Then, using their mining power advantage, they reorganized the blockchain by replacing the blocks that contained their original deposits, effectively erasing them from the ledger. As a result, the exchanges lost around $18 million worth of Bitcoin Gold.
The attack severely damaged Bitcoin Gold’s credibility. Several exchanges, including Bittrex, delisted BTG due to security concerns. The Bitcoin Gold team tried to strengthen security by implementing network upgrades, but their small hash rate remained a major weakness.
The 2020 Attack
Just two years after the first attack, Bitcoin Gold was hit again in January 2020. This time, the attackers successfully reversed 29 blocks, allowing them to execute another double-spending attack.
Although the financial losses from the second attack were smaller, the fact that Bitcoin Gold remained vulnerable proved that its security measures were still inadequate.
The repeated attacks significantly reduced trust in Bitcoin Gold, and its market value suffered. The project continued to operate but struggled to regain investor confidence.
2. Ethereum Classic (ETC) – 2019 & 2020 Attacks
Ethereum Classic (ETC) is the original Ethereum chain that continued its path after Ethereum’s hard fork following the DAO hack in 2016.
With a significantly lower hash rate than Ethereum, Ethereum Classic became an attractive target for attackers looking to exploit its network security weaknesses.
The 2019 Attack
In January 2019, Coinbase, one of the largest cryptocurrency exchanges, detected unusual blockchain reorganization on Ethereum Classic.
The exchange’s security team noticed that several transactions had been reversed, indicating that an attacker had gained majority control of the hash rate.
Further analysis revealed that over $1.1 million worth of ETC had been double-spent. The attacker used cloud mining services to rent mining power and conducted the attack without needing their own expensive hardware.
The incident prompted Coinbase to pause ETC deposits and withdrawals, forcing the Ethereum Classic community to acknowledge its security weaknesses.
The attack also sparked debates about whether smaller PoW blockchains could ever be truly secure.
The 2020 Attacks
Ethereum Classic suffered not just one but three separate 51% attacks in August 2020. These attacks led to more than 4,000 blocks being reorganized, making it one of the most severe blockchain manipulations ever recorded.
Each attack followed the same method:
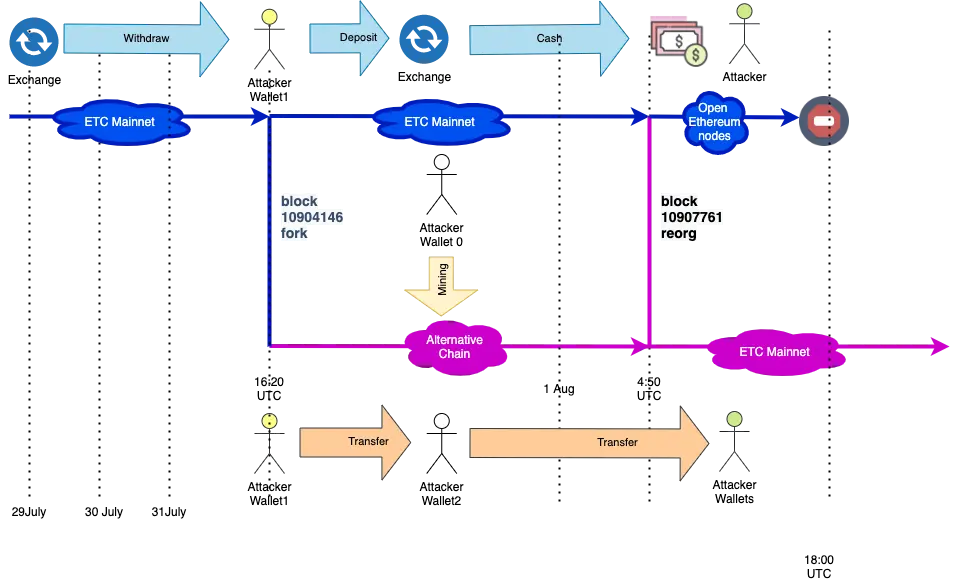
- The attackers rented hash power from NiceHash, a marketplace for cloud mining services.
- They privately mined an alternative chain while simultaneously sending large ETC deposits to exchanges.
- After their deposits were confirmed, they exchanged ETC for Bitcoin and withdrew their funds.
- Finally, they released their privately mined chain, which erased the original transactions, allowing them to keep both the exchanged Bitcoin and the original ETC.
These repeated attacks resulted in millions of dollars in losses and led exchanges like OKEx to increase the number of confirmations required for ETC transactions.
The Ethereum Classic community eventually implemented security upgrades such as MESS (Modified Exponential Subjective Scoring) to make 51% attacks more difficult, but the damage to the blockchain’s reputation was irreversible.
3. Verge (XVG) – 2018 Attack
Verge (XVG) is a privacy-focused cryptocurrency that suffered a unique and highly damaging 51% attack in April 2018.
Unlike other attacks that primarily focused on double-spending, the Verge attack exploited a flaw in the block timestamping mechanism, allowing the attacker to mine thousands of blocks within minutes.
This manipulation effectively gave the attacker control over block generation, allowing them to earn massive mining rewards. By the time the issue was detected, Verge had lost approximately $1.75 million worth of XVG.
The attack exposed severe weaknesses in Verge’s protocol, forcing developers to release emergency patches. However, these security flaws continued to raise concerns about the project’s long-term viability.
4. Bitcoin SV (BSV) – 2021 Attack
BSV is going through a massive 51% attack.
After an attempted attack yesterday, some serious hashing power was unleashed today at 11:46AM and attackers are succeeding.
Over a dozen blocks are being reorgd & up to 3 versions of the chain being mined simultaneously across pools.
— Lucas Nuzzi (@LucasNuzzi) August 3, 2021
Bitcoin SV (BSV), another Bitcoin fork led by Craig Wright, suffered a coordinated 51% attack in August 2021. The attack led to the reorganization of several blocks, which created confusion about the validity of transactions.
What made this attack particularly concerning was the complexity and scale. Blockchain analysts discovered that the attackers had been preparing for weeks, coordinating their mining power to execute the attack at the right moment.
Unlike other cases where attackers focused on double-spending, this attack was designed to destabilize the network, leading to speculation that it was politically or ideologically motivated.
The incident raised further concerns about the sustainability of BSV, which was already controversial due to its leadership and centralization risks.
The attack significantly reduced trust in Bitcoin SV, causing exchanges to temporarily halt deposits and withdrawals.
Can Bitcoin Be Attacked?
If you’re worried that China is planning a 51% attack to ‘kill’ #bitcoin watch this 2 minute video and you’ll sleep soundly tonight. pic.twitter.com/62ZkLMxli8
— Glenn Hodl (@glennhodl) June 28, 2021
Technically, yes, but it’s nearly impossible due to Bitcoin’s massive network size.
- Bitcoin’s hash rate is 400+ EH/s (exahashes per second).
- Controlling 51% would require billions of dollars in hardware.
- Electricity costs alone would make an attack financially unfeasible.
Most successful 51% attacks happen on smaller blockchains with weaker security.
How to Prevent a 51% Attack
Blockchains use several methods to reduce the risk of a 51% attack. Here are the most effective:
1. Increasing Network Hash Rate
A higher hash rate means more miners securing the network. The stronger the network, the harder it is for an attacker to gain majority control.
2. Switching to Proof-of-Stake (PoS)
Ethereum avoided 51% attacks by switching to PoS, where validators stake coins instead of mining. An attack would require controlling 51% of all staked ETH, which is incredibly expensive.
3. Checkpointing
Some blockchains use checkpoints, where transactions beyond a certain block cannot be reversed, preventing attackers from reorganizing the chain.
4. Stronger Consensus Rules
Some blockchains use ChainLocks (like Dash), which finalize blocks immediately, making attacks nearly impossible.
5. Higher Confirmation Times
Exchanges often require multiple confirmations for deposits. For example, Coinbase requires 35 confirmations for Ethereum Classic to prevent double-spends.
6. Mining Pool Decentralization
If too much mining power is concentrated in a few pools, an attack becomes easier. Encouraging more independent miners helps distribute power more evenly.
Is the 51% Attack a Real Threat?
51% attacks remain one of the biggest threats to PoW blockchains, especially smaller ones. While Bitcoin is safe, altcoins with low hash rates are still vulnerable.
The crypto industry continues to develop better security mechanisms, including PoS, ChainLocks, and checkpointing, to prevent these attacks.
If you’re an investor, always research a blockchain’s hash rate, mining power distribution, and security mechanisms before investing.
The future of crypto security depends on decentralization, innovation, and stronger consensus models to prevent these threats.
Key Takeaways
✅ A 51% attack happens when a miner controls over 50% of a blockchain’s mining power.
✅ It allows double-spending, transaction reversal, and blockchain manipulation.
✅ Bitcoin is nearly immune, but smaller blockchains remain vulnerable.
✅ Prevention methods include PoS, higher hash rates, and decentralized mining pools.
✅ Always research a blockchain’s security before investing or trading.